“Discover the impact and crucial role of robust security mechanisms in Industry 4.0. We simplified the required tools, and the international guidelines to safeguard your critical systems, data, and operations from evolving cyber threats with real-life examples and case studies.“
In December 2017, an unidentified power station in Saudi Arabia fell victim to a state-sponsored cyber-attack. The Triconex industrial safety technology, developed by Schneider Electric SE, was targeted by the state-sponsored notorious Triton/Trisis malware. The attack exploited a vulnerability in the Microsoft Windows operating system, and the consequences could have been catastrophic, risking the release of toxic gas and explosions. Fortunately, the safety systems intercepted the malware and entered a failed safe state, leading to a shutdown. The attack highlights the critical need for robust security measures to protect industrial safety systems.
Jump to Section:
Implications of Lacking a Secure Industry 4.0 System
Potential Risks of Security Failure in Industry 4.0 Networks
- Security Mechanisms for Protecting Industrial Automation Systems from CyberAttacks
- Industry 4.0 Networks: Essential Security Tools and Software Packages
- International Security Standards: Safeguarding OT and IT Networks
Future Trends
OT and IT Networks in Industry 4.0:
The integration of Operational Technology (OT) and Information Technology (IT) has revolutionized the industrial landscape in Industry 4.0. With interconnected industrial devices and enterprise networks seamlessly converging, organizations can enhance data exchange, optimize processes, and make informed decisions. However, it is crucial to recognize the potential threats and establish robust defense mechanisms to safeguard both OT and IT networks. This article explores the importance of secure networks in Industry 4.0, the implications of lacking security measures, and effective strategies for securing industrial automation systems.
Implications of Lacking a Secure Industry 4.0 System:
Inadequate security mechanisms in industrial environments pose significant security, social, physical, and intellectual consequences. To understand the severity of such security lapses, let’s examine five major security implications, each accompanied by a real-life recorded example.
Unauthorized Access and Control: Malicious actors can exploit vulnerabilities to gain unauthorized access and control over critical systems, leading to operational disruptions, safety hazards, or financial losses.
Real-life Incident: The Stuxnet worm in 2010 targeted industrial control systems (ICS), causing physical damage to centrifuges in an Iranian nuclear facility and disrupting their nuclear program.
Data Breach and Intellectual Property Theft: Lack of proper security measures can result in the compromise of confidential and proprietary information, leading to the loss of intellectual property, trade secrets, or sensitive customer data.
Real-life Incident: In 2014, a cyberattack on a German steel mill allowed hackers to gain access to the plant’s network, resulting in significant damage to a blast furnace. This incident highlights the vulnerability of industrial systems and the potential for data theft.
Disruption of Operations and Downtime: Cyberattacks or malware can disrupt operations, causing production delays, equipment failures, or complete shutdown of critical processes.
Real-life Incident: The NotPetya ransomware attack recorded in 2017 is considered one of the most devastating Cyber attacks in the history. The attack impacted several large companies worldwide and caused large-scale supply chain disruptions and financial losses due to halted operations.
Safety Risks and Physical Damage: Compromised security measures can expose personnel to safety risks, lead to environmental damage, or result in the physical destruction of equipment.
Real-life Incident: The Triton malware attack in 2017 targeted a petrochemical plant in Saudi Arabia, aiming to manipulate safety systems. Although the attack was detected and prevented, it highlighted the potential for severe safety risks and physical damage if successful.
Supply Chain Vulnerabilities: Inadequate security measures can introduce vulnerabilities across the supply chain, impacting multiple organizations and critical infrastructure.
Real-life Incident: The SolarWinds hack in 2020 compromised software updates, affecting numerous organizations, including the U.S. government. This incident resulted in wide-ranging impact of supply chain vulnerabilities and the need for robust security measures.
These real-life examples underscore the severity and consequences that arise from the lack of proper security mechanisms in both IT and OT networks. Implementing comprehensive security measures is crucial to safeguarding industrial automation systems, protecting critical infrastructure, and mitigating potential risks.
Potential Risks of Security Failure in Industry 4.0 Networks:
A security failure in Industry 4.0 networks can have significant repercussions, including physical damage, environmental harm, loss of human lives, financial losses, and reputational damage. Let’s explore these risks in detail:
Physical Damage: Attackers could cause extensive damage to the plant’s equipment and infrastructure, resulting in expensive repairs and lengthy downtime.
Environmental Damage: A successful attack on an industrial, oil & gas, or petrochemical facility could lead to the release of hazardous materials, posing risks to the environment and public health.
Loss of Human Lives: If safety systems fail to trigger emergency shutdowns, an attack could have catastrophic consequences, including the loss of human lives.
Financial Loss: Repairing the damage, investigating the attack, and implementing new security measures can incur substantial costs, leading to significant financial losses for the company.
Reputational Damage: Cyberattacks can tarnish a company’s reputation, resulting in lost customers, partners, and investors.
Securing your Industry’s OT and IT Networks from Malicious Attacks:
Industrial automation networks are comprised of two essential components: OT (Operational Technology) networks and IT (Information Technology) networks. OT networks are dedicated to controlling devices like SCADA systems, DCS, and PLCs, which actively monitor and manage industrial equipment and production operations. IT networks, on the other hand, handle data, applications, and communication services using servers, workstations, routers, and switches.
The distinction between OT networks and IT networks lies in their objectives, device types, and employed network protocols. OT networks prioritize real-time control and monitoring of industrial processes, while IT networks primarily focus on business process management and data handling.
From a cybersecurity perspective, OT networks are often more vulnerable to malware propagation due to the specialized nature of industrial devices and the prevalence of legacy systems that rely on open-ended protocols such as Modbus, Ethernet, and Profibus. To safeguard plant networks against potential threats, it is imperative for industries to implement tailored security measures.
Security Mechanisms for Protecting Industrial Automation Systems from CyberAttacks:
To enhance the security of automation systems, industries widely adopt layered security mechanisms. Each layered mechanism is designed to address specific types of cyber attacks. In the following sections, I will delve into these layered measures and provide insightful recommendations for their effective implementation. Additionally, I will highlight the tools and products available in the market that align with each security mechanism.
- Access Control: Implement robust access control mechanisms, such as role-based access control (RBAC) or attribute-based access control (ABAC). By defining and enforcing proper access rights, you ensure that only authorized personnel can access critical systems and sensitive data.
- Network Segmentation: Divide your network into smaller segments or zones, each with its purpose and level of security. This practice isolates critical systems and data, minimizing the potential impact of an attack and containing threats within specific segments.
- Firewalls and Intrusion Detection/Prevention Systems (IDS/IPS): Deploy firewalls to monitor and filter network traffic, allowing only authorized communication while blocking malicious attempts. Complement this with intrusion detection/prevention systems (IDS/IPS) that actively monitor network activity, detect anomalies, and proactively prevent potential attacks.
- Asset Management and Visibility: Maintain an accurate and up-to-date inventory of all devices, systems, and software within your OT and IT networks. This inventory provides valuable visibility into your network, supporting effective security management and enabling timely incident response.
- Encryption: Implement strong encryption mechanisms to protect sensitive data both during transmission and at rest. By encrypting your data, you add an extra layer of protection against unauthorized access or tampering.
- Secure Remote Access: As remote work and third-party collaborations become more prevalent, establish secure remote access solutions such as Virtual Private Networks (VPNs). These solutions enable encrypted and authenticated connections, allowing authorized individuals to access your network while maintaining strict control over access privileges.
- Security Patch Management: Stay vigilant about regularly updating and patching your devices, systems, and software. By promptly applying security patches and fixes, you address known vulnerabilities and reduce the risk of exploitation by malicious actors.
- Security Information and Event Management (SIEM): Implement a comprehensive SIEM system to gather, analyze, and correlate security events from various sources. SIEM enables you to detect potential threats, identify patterns of malicious activity, and respond swiftly to security incidents.
- Employee Training and Awareness: Foster a culture of security awareness among your employees through regular training programs. Educate them about potential risks, best practices, and how to recognize and respond to security incidents effectively. Empowering your employees to be proactive in safeguarding your network is key to a robust security posture.
- Incident Response and Recovery: Develop a well-defined incident response plan tailored to your automation systems. This plan should outline clear procedures for detecting, containing, and remediating security incidents. By having a structured approach in place, you can minimize the impact of security breaches, ensure business continuity, and facilitate a swift recovery process.
Remember, as industries embrace automation, prioritizing network security is vital to safeguarding operations, protecting sensitive data, and mitigating potential risks. By implementing the above-recommended security measures, you can establish a strong defense against evolving cyber threats and build a resilient automation ecosystem for your organization.
Securing Industrial Automation and Industry 4.0 Networks: Essential Security Tools and Software Packages:
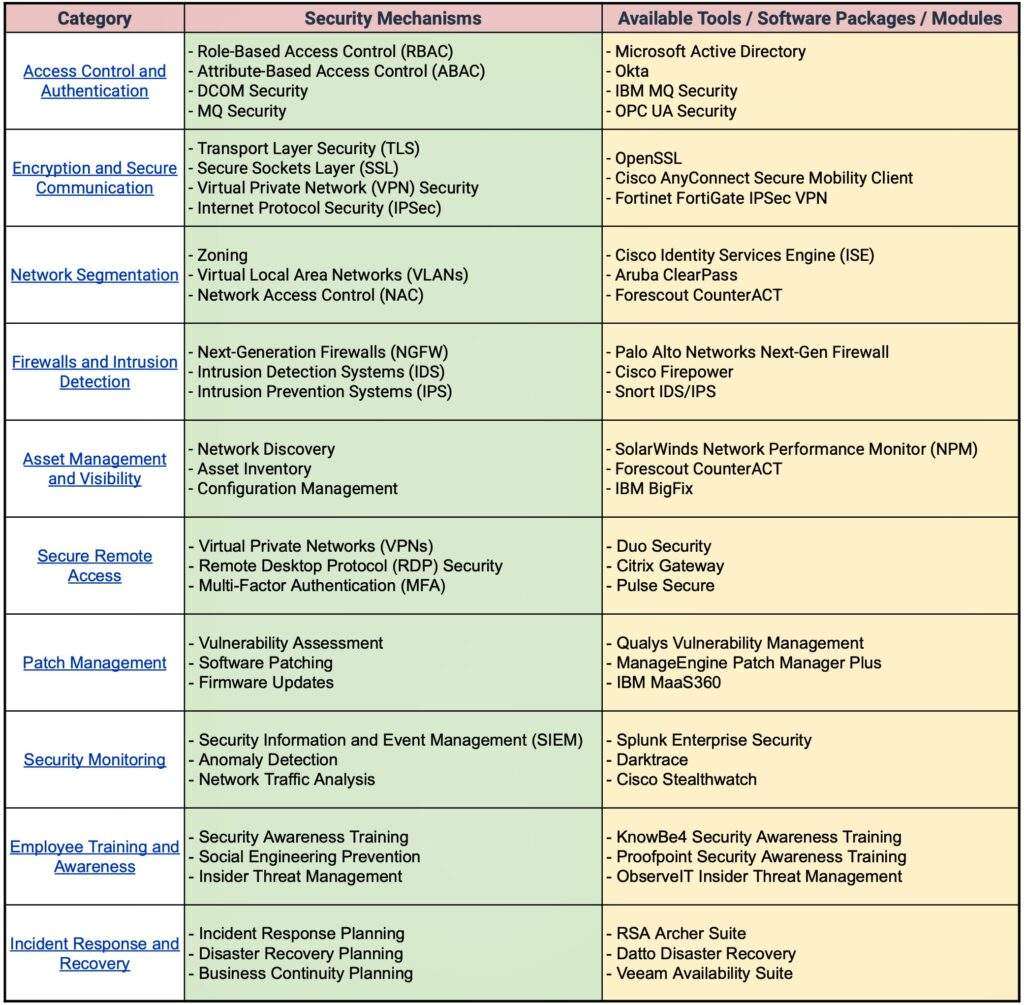
Note that the above list is comprehensive, and there are many other software packages and modules available in the market. The specific tools and software used by a company depend on factors specific to the project.
International Security Standards: Safeguarding OT and IT Networks
The following is a comprehensive list of Security standards commonly used as a reference in industrial environments for IT and OT security applications:
NIST SP 800-162 (Guide to Attribute-Based Access Control (ABAC)): Provides guidelines for implementing ABAC to limit access based on user attributes, enhancing access control in industrial environments.
Industrial Application: Using ABAC to control access to specific production lines in a manufacturing plant, ensuring only authorized personnel can operate critical machinery.
IEC 62443-3-3 (Industrial communication networks – Network and system security – Part 3-3): System security requirements and security levels: Defines system security requirements and specifies security levels for industrial automation and control systems.
Industrial Application: Applying IEC 62443-3-3 to assess and enhance the security of a power plant’s control systems, protecting against cyber threats and ensuring reliable electricity generation.
ISO/IEC 27001 (Information Security Management System (ISMS) – Requirements): Provides a framework for establishing, implementing, maintaining, and continuously improving an ISMS to protect information assets.
Industrial Application: Implementing ISO/IEC 27001 in an oil and gas refinery to secure critical data, such as operational logs and maintenance records, from unauthorized access or tampering.
ISO/IEC 27002 (Code of practice for information security controls): Offers guidelines for selecting, implementing, and managing information security controls to protect information assets.
Industrial Application: Implementing ISO/IEC 27002 in a smart city environment to protect the integrity and confidentiality of citizen data collected by IoT devices, such as smart meters and surveillance cameras.
NIST SP 800-57 (Recommendation for Key Management): Provides guidance on cryptographic key management practices to ensure the confidentiality, integrity, and availability of information.
Industrial Application: Implementing robust key management protocols in a chemical processing plant to protect sensitive formulas and intellectual property.
NIST SP 800-113 (Guide to SSL VPNs): Outlines best practices for implementing secure remote access using SSL VPNs to protect against unauthorized access.
Industrial Application: Deploying SSL VPNs in a logistics company to enable secure remote access for warehouse managers to monitor inventory and shipping processes from outside the facility.
ISO/IEC 27035 (Information security incident management): Provides a framework for managing information security incidents, including detection, reporting, and response.
Industrial Application: Implementing ISO/IEC 27035 in a transportation company to establish a structured incident response plan for quickly mitigating and recovering from cyberattacks on their vehicle tracking and routing systems.
NIST SP 800-61 (Computer Security Incident Handling Guide): Offers guidance on effectively detecting, analyzing, and responding to computer security incidents in industrial environments.
Industrial Application: Developing an incident response plan for a pharmaceutical manufacturing facility to protect sensitive formulas, prevent product tampering, and ensure the continuity of critical medication production.
By implementing these internationally recognized security guidelines in your industrial applications, you comply with most local, global, and client (if any) regulations to effectively mitigate risks, safeguard critical assets, and ensure the resilience and security of valuable industrial automation systems.
Summary and Future Trends:
Moving ahead into the future of Industrial Automation, with a growing number of innovations, the security threat landscape in Industry 4.0 is bound to evolve. Cyber attackers too are becoming more sophisticated and relentless around the world with respective motives.
However, the positive aspect is that increased awareness about the significance of security has driven extensive research and collaboration among experts, academia, and regulatory bodies. This has resulted in the development of international standards, best practices, and frameworks that provide valuable guidance for organizations to establish robust security postures.
To conclude, the importance of robust security mechanisms in Industry 4.0 cannot be overstated. Every organization must prioritize the implementation of comprehensive security measures to protect its critical systems, data, and operations. The risks associated with security failures in industrial environments can have far-reaching consequences, including operational disruptions, financial losses, reputational damage, and even safety hazards. Therefore, organizations should embrace cybersecurity as an integral part of their digital transformation journey and unlock the full potential of Industry 4.0 while mitigating risks and securing a prosperous future for industrial operations in the digital age.
-Lokesh Chennuru, Feed for Industry Digits
To stay up-to-date with the latest trends and best practices in the world of EV, consider signing up for our newsletter or following us on social media. We regularly share informative articles, industry news, and expert insights to help you stay ahead in this rapidly evolving field. By staying connected, you’ll have access to a wealth of resources and knowledge that can help you make the most of your IIoT projects.
Read More: Industrial IoT Projects: The Complete Sensor-Selection Guide. For Free!
We hope you found this article valuable. If you believe it could benefit others in your network, please feel free to share it with your colleagues and friends or on social media platforms. Sharing knowledge helps the entire community grow and stay informed.