“Increasing number of cyber attacks on EV charging stations are exposing vulnerabilities within the EVSE infrastructure, and posing potential risks for EV owners. Read more for Insights, and guidelines for industry and businesses.”
Electric vehicles (EVs) have gained popularity in recent years due to their low environmental impact and low operating costs. However, since 2022, 100+ automotive cyber-related incidents have been publicly reported, with EV charging identified as the primary emerging attack vector. Attacks have raised concerns over the cybersecurity of EV charging infrastructure, which could allow hackers to carry out distributed denial-of-service attacks or steal sensitive information.
Since EV chargers also operate similar to the Internet of Things (IoT) concept, it is essential for EVSE (Electric Vehicle Supply Equipment or Charging Station) operators and EV owners to understand how hackers exploit vulnerabilities in communication protocols and take alert, proactive measures to remain immune from future attacks. In this article, we will dwell into:
- EV Communication network, Cyber Attack modes, and the transmission
- Impact of cyber attacks
- Preventive measures – For governments, startups, and private players engaged in building the EV infrastructure
By the end of this article, readers will have a better understanding of the risks associated with EV charging station cyber attacks and the ways to mitigate them.
The Need to understand EV Charger Cyber Attacks and their Impact:
The accelerated expansion of EVs and the EVSEs to be installed at workplaces and publicly-accessible locations has provided hackers to easily access EVSEs resulting in serious risk for EV owners and EVSE operators. These cyber-attacks on Charging Stations can have both Localized and Widespread impacts:
Local Impacts:
- Theft of PII (Personal Identifiable Information, such as your name, address) and financial information (credit card, bank details)
- Damage to batteries and other EV Components (by over/under charging, using non-compliant wattage/rate of charge)
- Failure to Charge vehicle
- Loss of EVSE service availability
Wide-spread Impacts:
- Selling PII and Financial information
- Shutdown of an entire EVSE Charging network
- Exposure of upstream and partner IT networks
- Misconfiguration of EVSE creating damaging conditions
- Loss of consumer confidence in EVSE ecosystem
- Bulk power system impacts
These attacks can also have ripple effects on other critical infrastructure sectors, including transportation, energy, emergency services, and manufacturing industries. As a result, the economy and daily life can be significantly impacted. Therefore, the aim of this article is to provide an overview of Charging Station Cyber attacks, enabling readers to be better prepared to address them.
Let us first briefly examine the components and communication network of EV charging stations.
EV Charging Stations (EVSE) – Components and Communication Networks:
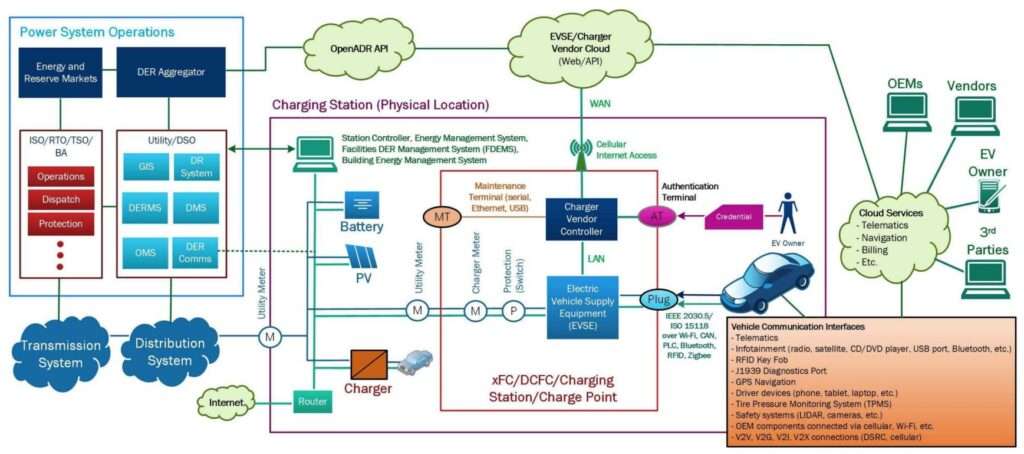
Electric vehicle charging stations, also known as Electric Vehicle Supply Equipment (EVSE), involve various components and communication networks that enable electric vehicles to charge. Every layer of this network – starting from Grid/Power system operators, EV charging stations, Cloud services (OEMs, vendors, third party, etc.), EV to Vehicle interface, and in-vehicle communication can be a potential target for cyber attacks. The following image depicts the Electric vehicle communication ecosystem with EVSE components and external entities:
Understanding Cybersecurity Vulnerabilities:
To simplify EVSE cybersecurity assessments and vulnerabilities, we have categorized potential target vector modes by the interface type:
- EV-to-EVSE (Charger) Interfaces
- EV Owner (Payment and Charging) Interfaces
- Cloud and EVSE Internet Interfaces
- EVSE Maintenance Interfaces
#1. EV-to-EVSE Interface Vulnerabilities:
EV (Electric Vehicle) to EVSE (Charging station) interface includes the EVSE connectors (i.e., chargers, couplers, or plugs), often specified range in terms of power level, type, and underlying communication technology (Levels 1, 2, Fast charging, and proprietary protocols).
Reported Attacks on EV-to-EVSE Interface:
Using low-cost hardware and software, hackers reverse-engineered the signals and circuits on an EV and a J1772 charger, the most prevalent interface for managing EV charging in North America. By creating a “man-in-the-middle” (MITM) device that spoofed signals between the charger and the vehicle, the hackers were able to disrupt the vehicle charging process successfully. The attackers performed three manipulations using the MITM device, including limiting the rate of charging, blocking battery charging, and overcharging the vehicle.
EV-to-EVSE Attack Demonstrations:
Several demonstrations have shown how hackers can steal credentials or manipulate charging sessions through the EV-to-EVSE connection. Köhler and his research team demonstrated the Brokenwire attack, which could wirelessly abort charging sessions by disrupting PLC communications. Using software-defined radios (SDRs) with less than 1 W of power, they could successfully abort CCS charging sessions remotely from a distance of 47m. This Brokenwire attack was successful on all seven vehicles and 18 EVSEs that the researchers investigated, highlighting the potential vulnerabilities in the electric vehicle charging infrastructure.
The list of such successful EV-to-EVSE Attack demonstrations is presented here, depicting the vulnerabilities in the EV Charger Communication interface.
Read More: Gas to Charging Stations: Innovation, Opportunities, & Challenges for EV Charging Infrastructure
#2. EV Owner (Payment and Charging) Interface Vulnerabilities
Public EVSEs provide various methods for authenticating a charging session through RFID tags, smartphone NFC, or credit card chip/swipes. However, the driver-user interface on the EVSE can be a significant target for cyberattacks. Hidden maintenance menus or password-protected service options are often available on these interfaces in addition to standard functionality. If compromised, these systems can allow hackers to leak personal data, disable charging, change prices, or disrupt the operations of the EVSE.
Reported Attacks on EV Owner (Payment and Charging) Interface:
Taiwan-based car rental platform iRent suffered a data breach, exposing customers’ PII. The leak included the full names, addresses, driver’s licenses, and payment details. About 400,000 iRent clients have been identified as at risk from the leaked PII data, prompting iRent to offer compensation packages to these affected clients. The details of this compensation are not yet clear.
EV Owner Interfaces – Attack Demonstrations:
At the Chaos Communication Congress, Mathias Dalheimer, a researcher at the Fraunhofer Institute for Industrial Mathematics (ITWM), demonstrated how RFID cards could be cloned, resulting in other debit or credit cardholders being billed for charging sessions. This highlighted the weak security practices in billing transactions and RFID card data storage in public charging infrastructure.
The list of such successful EV Owner Attack demonstrations is presented here, depicting the vulnerabilities in the EV Payment and Charging interface.
Read More: IoT, IIoT, Industry 4.0, and Industrial Automation: Myths, Similarities & Differences
#3. Cloud and EVSE Internet Interface Vulnerabilities
EVSEs are often connected to one or more internet services, enabling the exchange of telemetry data and control to EVSE vendors or third-party cloud environments to facilitate billing operations and enable grid operators to interact with EVSE equipment, as illustrated in the communications Figure (above). Although EVSE communications are often proprietary, several OPEN End protocols, such as Open Charge Point Protocol (OCPP), Open Smart Charging Protocol (OSCP), IEEE 2030.5, OpenADR, Message Queue Telemetry Transport (MQTT), and Building Automation Control network (BACnet), are used by EVSE devices on the market. Of them, OCPP is widely used to connect EVSE to third-party EVSE monitoring and control networks. Though OCPP Version 2.0.1 is available, Version 1.5 and 1.6 are still widely used in the field, which is severely vulnerable to Cyber Attacks.
Reported Attacks on Cloud and EVSE Internet Interfaces
An EV charging station in the Isle of Wight, UK, was hacked, replacing displayed content with pornographic material. Though the council issued an apology for the inconvenience, the attack affected several charging stations using chargers from the GeniePoint network, covering much of the UK. Some EV owners also experienced high voltage fault codes, causing their car’s charging system to shut down, leaving them stranded at the charging station.
Cyber Attack Demonstrations on Cloud and EVSE Internet Interfaces:
Kaspersky Lab demonstrated how the ChargePoint smartphone application could remotely tamper with a charging session via Wi-Fi using a buffer overflow in the web server Common Gateway Interface (CGI) binaries. This vulnerability presents a significant risk. It could result in charging sessions being stopped or the maximum charging current being increased beyond the circuit rating, potentially tripping the breaker, overheating the wiring, or, in the worst case, causing a fire.
Pen Test Partners discovered that the Shenzen Growatt network, consisting of 2.9 million devices, only required a predictable serial number and an unvalidated username to lock and unlock the charger. The locking action could stop all charging processes, as indicated.
The list of other attack methods on the Cloud and EVSE Internet Interfaces is presented here, depicting the vulnerabilities in the interface.
#4. EVSE Maintenance Interface and Hardware/Software Vulnerabilities
Modern EVSEs, particularly DCFCs, use multiple circuit boards to communicate through various protocols such as ethernet, serial, and analog, among others. These inter-module communications are often unencrypted and can provide easy access to the internal network just by connecting to them. Additionally, open physical ports such as USB serial ports and JTAG headers are sometimes available for equipment debugging but are mostly left open, providing opportunities for cyber adversaries to disrupt or monitor the equipment operations.
Reported Attack Demonstrations on Maintenance Hardware/Software Vulnerabilities:
Schneider discovered seven vulnerabilities in EVlink City (EVC1S22P4 and EVC1S7P4), Parking (EVW2, EVF2, and EVP2PE), and Smart Wallbox (EVB1A) devices. Though the bug was later fixed, these vulnerabilities could have allowed remote attackers to impersonate charging station users or carry out actions on their behalf by submitting malicious parameters to the charging station web server.
Findings and the list of other attack demonstration methods on the EVSE Maintenance Hardware/Software are presented here: Link
Cyber Attack – Transmission Modes:
All EVSE Cyber attacks can result in a range of risks to Electric Vehicles (EVs) and Grids, and the transmission can be through all three attack vector modes:
- Vehicle-to-Charging Networks (V2C) — Charging fraud through vehicle impersonation, compromising the integrity and security of charging systems.
- Grid-to-Vehicle (G2V) — Cyberattacks targeting grid charging networks, disrupting the ability to charge EVs.
- Grid-to-Fleet (G2F) — Charging stations attacking multiple vehicles.
Let us now examine the impact of Cyber Attacks on EVSEs.
Impact of Cyberattacks on Grids, EVSEs, EVs, and EV owners:
The impact of cyber attacks on EVSEs can be severe, ranging from security implications – such as compromise on Confidentiality, Integrity, and Availability of EV charging stations, to physically affecting the Grid, EV or the EV operator (owner). In the following table, we highlight the potential impacts of various cyber attacks on EVSEs.
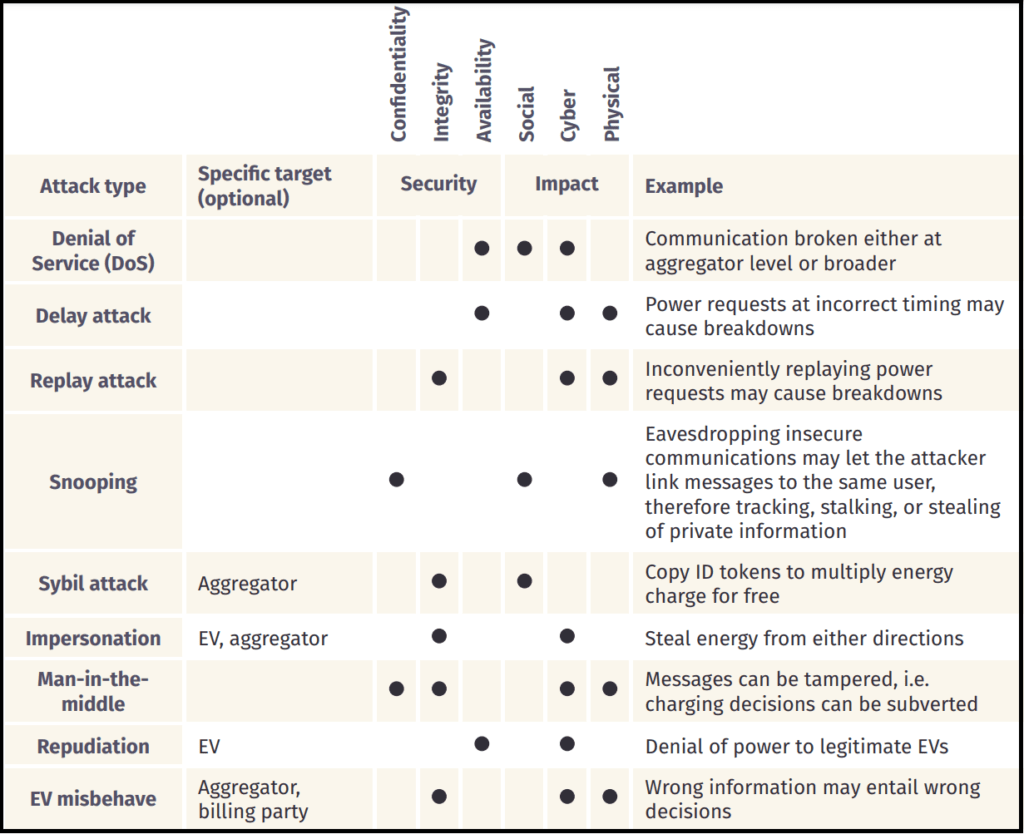
Preventive measures – Government and EV Charging Network Shareholders:
The rise in popularity of EVs has led to significant security vulnerabilities in charging infrastructure. Most EV charging stakeholders are still in the early stages of implementing advanced cybersecurity platforms and are not yet required to follow regulations and standards similar to UNECE WP.29 R155 and ISO/SAE 21434. The industry should quickly adopt the following best practices:
A. For Business Network & Operations:
- Implement secure coding practices, including integrity checks of code repositories and version control
- Use separation of privilege for all EVSE-related operations
- Ensure cybersecurity best practices like the NIST Cybersecurity Framework are used for internal assessments, cyber hygiene, patching, supply chain, and insider threat mitigations, etc.
B. EVSE Security:
- Implement tamper-detection sensors and alarms on EVSE Enclosures
- Prioritize alarms and ensure timely actions on critical log events
- Encrypt all information storage devices within the EVSE
C. EVSE Network:
- Use network segmentation and VLANs to isolate EVSE installations
- Install firewalls and IDSs at key network locations
- Encrypt all network traffic using FIPS 140-2 compliant cryptographic module
- Disable unnecessary services and ports
- Ensure proper defense in depth by limiting external access to EVSE devices, to only authorized users and devices using access control technologies
D. EVSE Operations:
- Validate all network traffic and EV inputs before routing them into the EVSE OT Network
- Utilize secure trust principles such as Hardware/Software signing, secure boot, and secure firmware and software to update processes
- Manufacturers and developers should follow secure software development practices.
Read More: Sandia National Laboratories Cybersecurity for Electric Vehicle Charging Infrastructure
Read More: Is Slow Charging better for your EV Li-ion Battery? Proven here
Preventive measures – For EV owners to safeguard from cyber attacks on EV charging stations:
- Use trusted charging stations and verified apps from official sources.
- Use secure connections: When using public charging stations or accessing them through an app, make sure the connection is secure. Avoid using public Wi-Fi networks to access charging station apps.
- Keep software up-to-date: Keep your EV’s software and charging station apps up-to-date to ensure that any known vulnerabilities have been addressed.
- Use strong passwords and cyber-security features such as two-level authentication.
- Monitor payment transactions for any unauthorized charges or suspicious activity.
-Lokesh Chennuru, Feed for Industry Digits
To stay up-to-date with the latest trends and best practices in the world of EV, consider signing up for our newsletter or following us on social media. We regularly share informative articles, industry news, and expert insights to help you stay ahead in this rapidly evolving field. By staying connected, you’ll have access to a wealth of resources and knowledge that can help you make the most of your IIoT projects.
Read More: Industrial IoT Projects: The Complete Sensor-Selection Guide. For Free!
We hope you found this article valuable. If you believe it could benefit others in your network, please feel free to share it with your colleagues and friends or on social media platforms. Sharing knowledge helps the entire community grow and stay informed.